Worldwide cyberattacks are on the rise these days. If we understand it with the help of statistics, corporate networks are seeing a 30% increase in weekly attacks from Q2 2023 to Q2 2024 and a 25% jump compared to Q1 2024. If we consider the average, organizations face about 1,636 attacks each week. This indicates that cybercriminals are becoming clever day by day. Therefore, these bad guys make it tough for businesses to be safe and secure. So, it’s vital for firms to understand COBIT framework to keep their personal data safe from cyberattacks.
In this blog content, we covered the meaning and importance of COBIT. Then, we discussed COBIT as a cybersecurity framework to help readers understand it more deeply. Let’s begin and learn!
Definition of COBIT
The Control Objectives for Information and Related Technologies are shortened to COBIT. It was specially invented for managers and to support them in their work. It bridges the critical gap between business risks, technological concerns, and control needs. COBIT is a widely accepted standard that may be used by any firm in any sector.
It ensures a firm’s information systems’ dependability, management, and quality. It ensures that information technology (IT) activities align with the firm’s business goals. The COBIT IT governance framework gives a common language for compliance auditors, business executives, and IT specialists. So, communication about business and management goals becomes easy.
Importance of COBIT
For firms that want to manage their IT efficiently, COBIT is a must. It gives simple guidelines to align IT with business goals, helping to reduce risks and confirm compliance. By utilizing it, firms can improve their IT processes, make better decisions, and support their overall strategies.
It focuses on delivering value to stakeholders and encourages ongoing improvement, making it a valuable tool in this tech-savvy world.
COBIT as a Cybersecurity Framework
It is a strong cybersecurity framework. Its in-depth approach to risk management makes it function smoothly as a cybersecurity framework. Firms can identify significant threats and vulnerabilities within their IT systems and can carry out controls to minimize those risks with the help of COBIT.
It observes people and procedures in addition to tech-related aspects. So, it helps to make sure that cybersecurity is woven into the fabric of the firm’s operations.
It provides a set of smart practices and guidelines that firms can follow to enhance their cybersecurity efforts. It has involved controls related to security management, incident response, and continuous monitoring. This structured approach allows firms to check their current cybersecurity maturity, identify gaps, and prioritize improvements.
It is basically a governance framework. Its principles and practices make it a precious tool for improving a firm’s cybersecurity efforts. It helps to design a safer and more resilient IT environment.
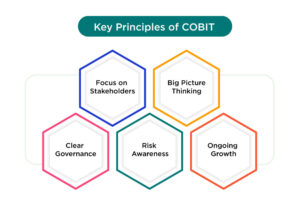
Key Principles of COBIT
- Focus on Stakeholders: IT department goals and business needs must match to keep everyone happy.
- Big Picture Thinking: Processes, people, and technology must work smoothly in collaboration with each other.
- Clear Governance: Promotes transparency and responsibility so everyone knows their roles.
- Risk Awareness: Helps identify potential dangers and find ways to minimize them for better security.
- Ongoing Growth: Encourages measuring performance and adjusting to stay relevant and effective.
Final Thoughts!
COBIT is vital for firms who aim to strengthen their IT governance and cybersecurity. It provides easy guidelines and a wide approach, and so it helps businesses align their IT strategies with their aims. Also, it aids in effectively managing risks in business security. Embracing this framework can lead to better decision-making and a stronger firm in today’s challenging tech-savvy era.
Cheers! We are thankful that you read our blog till the end. We hope our content will enhance your knowledge and help you secure your business with COBIT.
It seems you are interested in tech-related content, so we have more tech-related content for you on our website. So, visit us at HiTechNectar.
You May Also Like to Read –
Application Integration and Data Security: Ensuring Safe and Compliant Data Handling