NAS Encryption and its best practices ensure security from unauthorized users accessing confidential information. Moreover, encryption is one of the top solutions to secure data on network-attached storage.
According to Cybersecurity Ventures, “Global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015. This represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, is exponentially larger than the damage inflicted from natural disasters in a year and will be more profitable than the global trade of all major illegal drugs combined.”
Further, confidential data includes credit card information, intellectual properties, PII, etc., requiring protection. Compliance bodies like GDPR and HIPAA also use encryption to safeguard individuals and their records from potential threats. Therefore, if hackers and cyber criminals gain access to specific files or drives, encryption renders the data unreadable without a cryptographic key.
However, NAS encryption is a complex process, and its best practices can ensure the protection of confidential data. Hence, this article will discuss NAS encryption and its best practices that businesses must know.
Understanding NAS Encryption and its Best Practices
What is NAS?
NAS stands for Network Attached Storage. It refers to a data storage device that integrates with a network to store and access data from a central location. A NAS device connects to a network to provide access for on-premise and remote users. It also uses a VPN to encrypt NAS’s data.
According to IBM, “NAS (network-attached storage) refers to a file-level storage server connected to a computer network, providing data access to a group of users on that network. A NAS system connects via an Ethernet network and has redundant data structures for resiliency. It’s designed to be an affordable and easy-to-maintain network storage option.”
Top Safe and Secure NAS
-
- QSAN XN3004T NAS Drive for Full System Encryption
- ioSafe 1019 NAS Drive for Fireproof, Waterproof Protection
- Synology UC3200 NAS Server for Dual Active-Active System Redundancy
How does NAS work?
NAS stores data in files and manages them through folders, using an arrangement within the directories and sub-directories. It also provides a solution to collect more extensive data sets. Hence, here are the following components:
-
-
Network:
Network refers to devices integrated using an IP address with a local area network (LAN) or an Ethernet network.
-
NAS box:
Moreover, this hardware component offers its IP address that incorporates a NIC(network interface card), power supply, processor, memory, and storage systems. Further, the NAS box works as a head to integrate and analyze queries from the device to the storage system.
-
Storage:
The storage device is a suite of drives in the NAS box that stores and manages data. The storage generally uses a RAID (Random Array of Independent Disks) structure. It also deploys and copies data sets through various drives. As a result, it leads to data redundancy as a backup precaution. Hence, it enhances the performance and offers higher storage capacity.
-
Operating System:
NAS storage is a complete operating system compared to local storage. Further, the operating system helps execute data management solution capabilities and enables users to access files.
-
Software:
NAS box manages devices, monitors data, and uses pre-built solutions to file transfer queries.
-
A blog by IBM about the comparison between SAN and NAS explains, “When a user makes a request for a file stored on a NAS, the request is sent to the NAS box, the request is managed by the operating system and software, while the data is retrieved using protocols, such as SMB (server message block) — an application-level protocol used for shared access to files — or NFS (network file system) — which allows users to view, store and update files in a remote system. The data is then sent in packets to the user’s device using the TCP/IP protocol via a central server or switch.”
Here are some common use cases of NAS
Here are some general uses cases of NAS:
-
- File Integration and Storage: The initial application of NAS in various businesses is integrating and storing files. It also helps compress several file servers to manage and create space easily.
- Systematizing Files: NAS is also a great solution to store larger file sets. It also helps users easily navigate and access systematized files.
- Big Data: NAS uses its capabilities to store and analyze larger amorphous data files. It also implements analytics and uses ETL (extract, transform, load) solutions for collaboration.
Challenges in NAS Security
- Firstly, not all businesses execute safe and invulnerable security practices. As a result, it leads to threats and renders the data vulnerable to hackers and cybercriminals. Therefore, NAS security solutions are inadequate for data integrity and require encryption and its best practices.
- Moreover, there is a significant increase in networking devices and systems with the rise of IoT. Further, experts raise their concerns regarding data vulnerability in IoT devices. According to Greg Schulz, a senior advisory analyst with StorageIO “Even if the networked storage is on a separate network for data access than those used by IoT devices, infected data could get in from a compromised device if an IoT device is set up to access a NAS file, or object and blob storage.” Therefore, it threatens the integrity of NAS devices and their potential to be attacked by cybercriminals.
- NAS devices also face issues with malware and viruses. There have also been security breaches by victimizing drives and leveraging loopholes within the system.
- Further, Command Injection enables attackers to seize control of NAS devices. As a result, it gives them entitlement and prerogatives that only administrators have over the files. Above all, NAS devices are unable to gain complete security against Command Injection attacks.
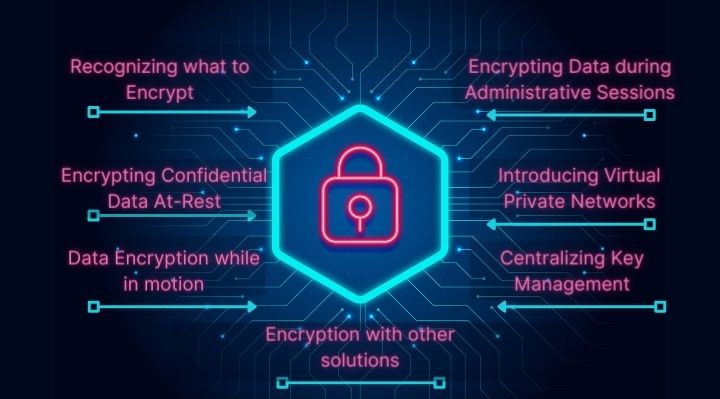
Here are the 7 NAS Encryption Best Practices that secure Data
-
Recognizing what to Encrypt:
Data encryption and decryption often lead to slower performances in the system. Therefore, businesses must categorize the data and files that are more sensitive and confidential. Moreover, encrypt the data that require additional security. It is also necessary to encrypt the data governed by regulatory and compliance bodies. Hence, one of the best practices for NAS is recognizing and categorizing data that requires encryption.
-
Encrypting Confidential Data At-Rest:
Data At-Rest stores data within NAS devices than transmitting it to various sources. That is to say; it includes pivotal data sets in the device that do not need constant transferring. Therefore, one of the best practices in NAS encryption ensures the security of the data in case of loss or theft of the device.
-
Data Encryption while in motion:
Transferring and sharing data often face threats of confiscating or extorting the data for information. Moreover, data encryption prevents cybercriminals from accessing sensitive information during transference. Further, with the rise in remote work opportunities, data encryption in NAS devices ensures security without authorized domains. Therefore, it secures data from negligent scenarios that may threaten the integrity of the data and files.
-
Encrypting Data during Administrative Sessions:
Administrators constantly access NAS systems to systematize and manage components that integrate with remote devices. It is important for businesses to understand that administrative access may also be unsafe. In other words, while transferring the data from various sources, hackers may gain access to the data via interception. Hence, encrypting administrative sessions help protect sensitive data from breaches and other threats.
-
Introducing Virtual Private Networks:
VPNs are solutions that encrypt data that connect and network through the internet. It also conceals insights about sessions and generates an additional layer of security for remote access. As a result, VPNs have become a pivotal part of NAS encryption for remote devices and connectivity.
-
Centralizing Key Management:
Most importantly, cryptographic keys play a pivotal role in encrypting and decrypting confidential information. Further, key management refers to monitoring processes that systematize, secure, store, and back up encryption keys. Creating, allocating, storing, renewing, and eliminating cryptographic keys is also important. Moreover, these capabilities require a centralized key management structure to monitor and secure keys. Further, key management is one of the best practices in NAS encryption as it accounts for regulatory and compliant rules. It is also privy to various protection and governing laws for encrypting data.
-
Encryption with other solutions:
Encrypting data may alone not be enough to protect and secure sensitive data. That is to say; data security requires multiple layers and processes to protect information. Therefore, data encryption must be integrated with other solutions to offer a more robust security structure.
Conclusion:
In conclusion, NAS Encryption and its best practices offer opportunities for businesses to protect data from illicit activities. It also renders the data unreadable and inaccessible using cryptographic keys that change regularly.
You May Also Like to Read:
Encryption as a Service Explained in Detail
Everything you need to know about Decentralized Storage Systems
What does DPM Stand for? DPM Technology is Explained in detail.