IoT and Quantum Computing are technological phenomena that are shaping businesses and industries. Moreover, integrating IoT and Quantum Computing solutions evolve ecosystems to offer optimum commercial practices. The emergence of these two phenomena offers revolutionary advancements.
Further, Quantum Computing introduces avant-garde encryption algorithms for resilient security solutions in IoT systems.
Therefore, MarketsandMarkets states, “The global IoT Security Market size to grow from USD 14.9 billion in 2021 to USD 40.3 billion by 2026, at a Compound Annual Growth Rate (CAGR) of 22.1% during the forecast period.” The report further states, “ IoT security comprises various smart solutions, such as device authentication and management, secure connections, and data loss prevention. These solutions, integrated with IoT devices, provide real-time protection from threats. Connected devices can give businesses a real boost, but anything that is connected to the internet can be vulnerable to cyber-attacks.”
According to Maurizio Di Paolo Emilio, a Ph.D. in Physics and a Telecommunication Engineer, “With the advent of quantum computers, modern encryption algorithms are undergoing an evolution that will significantly change their current use.”
Therefore, a prime prospect to secure IoT devices, components, and networks is Quantum Computing. Although amalgamating the two technologies is not, its practical applications now appear more likely.
Hence, the article will explain the evolutionary alliance between IoT and Quantum Computing.
IoT and Quantum Computing Working towards a Better Security
What is Quantum Computing?
According to IBM’s definition, “Quantum computing is a rapidly-emerging technology that harnesses the laws of quantum mechanics to solve problems too complex for classical computers.”
That is to say, quantum computing is a computational model that leverages the capabilities of Quantum Mechanics. Moreover, quantum states like superposition, interference and entanglement play a pivotal role in computing. It also introduces innovative theories to classical computing systems.
Further, the “quantum” in Quantum Computing describes the use of quantum mechanics to derive results. In physics, the term “quantum” also refers to the smallest possible unit of a physical object. It also contains references from atomic and subatomic particles like electrons, neutrons, and protons.
According to a study by Fortune Business Insights, “The quantum computing market is projected to grow from $486.1 million in 2021 to $3,180.9 million in 2028 at a CAGR of 30.8% in the forecast period, 2021-2028.”
Pivotal Aspects of Quantum Physics that enable Computing
-
- Superposition
- Entanglement
- Interference
What is a Qubit?
A qubit refers to the standard unit of measuring information within quantum mechanics. Moreover, qubits are to Quantum Computing what bits are to Classical Computing. Although both qubits and bits have varying characteristics. For instance, bits are binary and represent alignments using 0s and 1s. On the other hand, qubits comprise superpositions regardless of their state.
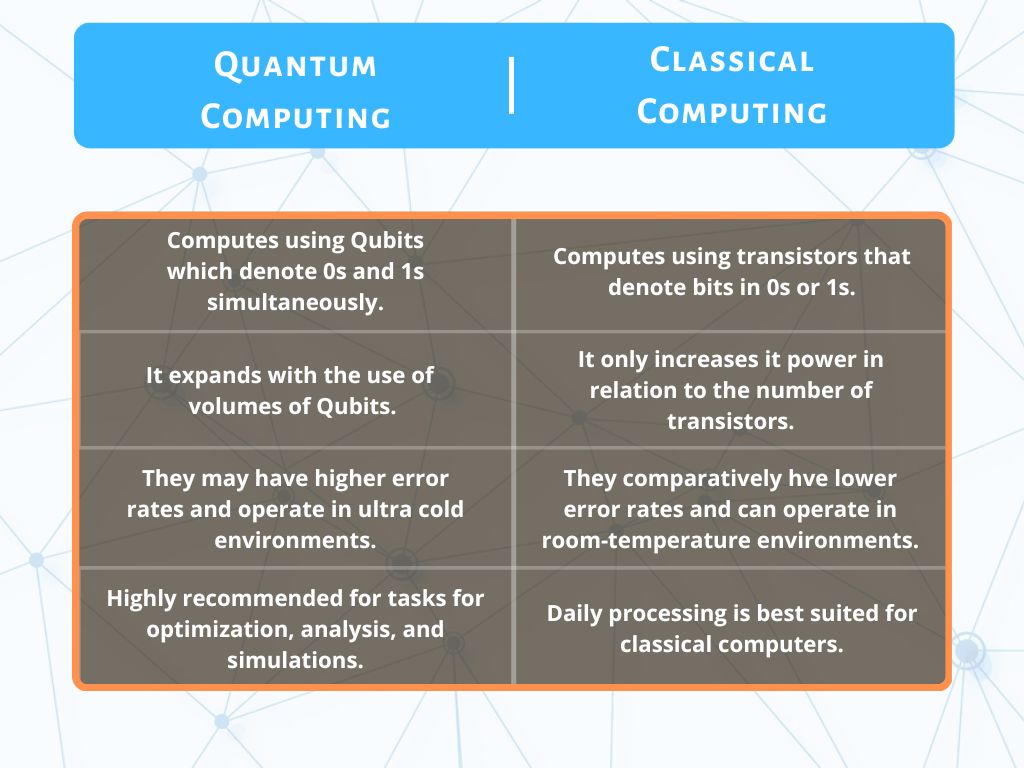
Comparison between Quantum Computing and Classical Computing
Firstly, Classical Computing derives its principles from Boolean Algebra which represents operations using binary numbers “0” and “1”. Moreover, it exclusively generates data in a binary status regardless of time or bits. Further, every capacitor or transistor is denoted in either 0s or 1s before altering states within a billionth of a second. Although there is a restraint on the swiftness of devices between the states. Therefore, advancing to smaller and more rapid circuits leads to restraints of the physical components.
As a result, with the limitation of classical laws of physics, quantum physics gain the upper hand. That is to say, Quantum Computing significantly exceeds the performance of Classical Computing. Moreover, it analyzes information in a different mechanism in comparison to Classical. Therefore, atomic and subatomic particles like electrons and photons use their characteristics of charge or polarization. As a result, each particle is a qubit or quantum bit that acts on the basis of Quantum Mechanisms. Further, using the qubits enhances its capabilities the more interconnections it makes in the network. It also represents its dominance as it increases with the number of transistors.
Applications of Quantum Computing
- Quantum Simulation:
Quantum simulation refers to the capabilities of systems to model other systems using quantum mechanisms while computing. Moreover, it proves that quantum computers can easily manage other systems’ complex and ambiguous properties. For example, quantum systems simulate photosynthesis, superconductivity, and compound molecular constructions.
- Quantum Cryptography:
Classical Cryptography like RSA (Rivest-Shamir-Adleman) generally uses its capabilities to secure data transmission. Although it depends heavily on the refractory of issues like integer factorization or distinct logarithms. As a result, quantum computers can offer solutions for these issues with maximum efficiency.
- Quantum Optimisation:
Optimization refers to searching for a faster and optimum solution for problems for specific outcomes. Further, science and industry often make decisions depending on factors like cost, quality, and time. Therefore, with the right solution, all these factors can be optimized. Moreover, quantum algorithms with classical computers help find better solutions. Therefore, it provides more preferable methods to manage complex systems.
- Quantum Machine Learning:
Machine Learning offers unique and revolutionizing solutions for classical computing to the world of sciences and businesses. Although training and developing machine learning models require excessive computing costs. Therefore, quantum computing offers divisive solutions for swift machine learning to gain optimum advances.
- Quantum Search:
For example, quantum algorithms from 1936 drastically increased the speed of processing unstructured data searches. Moreover, it performs the search in fewer steps than classical systems.
What is IoT?
Oracle defines IoT as, “The Internet of Things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet. These devices range from ordinary household objects to sophisticated industrial tools. With more than 7 billion connected IoT devices today, experts are expecting this number to grow to 10 billion by 2020 and 22 billion by 2025. Oracle has a network of device partners.”
That is to say, IoT, or the Internet of Things is a system of interconnected devices and networks that help process, transfer, and store data. Moreover, it uses sensors and unique identifiers (UIDs) to mitigate human-to-human and human-to-machine interference requirements.
Further, the “thing” in the Internet of Things refers to a user, device, or network that connects to the internet. Moreover, businesses from various industries use IoT to execute multiple tasks with maximum efficiency to deliver quality solutions, services, and products.
How do IoT Systems work? What are the pivotal Components?
All IoT systems include and integrate four discreet components. These components are Sensor/Devices, Interconnectivity, Data Analysis, and User Interface. Moreover, it is important to understand each component and its characteristics within the system.
-
Sensors/Devices:
Firstly, all sensors and devices gather data from their respective ecosystems. Moreover, the data may be simple or complex depending on their functions. For instance, data from an image would provide simple data in comparison to a video that may offer a complex structure.
-
Interconnectivity:
Further, interconnectivity refers to the transference of data to the cloud or network. Moreover, the sensors connect to the cloud and transfer data using various mechanisms. Therefore, the devices and sensors’ connection to the internet or ethernet depends on the power intake, range, and bandwidth. Hence, the stronger the connection to a network the stronger the interconnectivity to sensors and devices.
-
Data Analysis:
According to IoT Analytics, “In 2022, the market for the Internet of Things is expected to grow 18% to 14.4 billion active connections. It is expected that by 2025, as supply constraints ease and growth further accelerates, there will be approximately 27 billion connected IoT devices.” The report further states, “The previous estimate for 2021 was 12.3 billion connected IoT devices; the previous forecast for 2025 was 27.1 billion connected IoT devices.”
As a result, the increase in interconnected devices directly impacts the data the devices collect. Further, once the cloud obtains the data it is imperative to process and analyze the data. Moreover, the data analysis depends on the complexity, source, and confidentiality.
-
User Interface:
Further, post the analysis of data, it needs to translate into a simple format for the user to comprehend it. The user may also get notification of the results via alert systems regarding the analysis. Moreover, it helps the user to proactively check devices and their status regarding the data.
The Various Security Issues in the IoT Systems
Ponemon Institute’s Proofpoint’s 2022 Cost of Insider Threats Global Report states, “The 2022 report includes survey responses from more than 1,000 IT professionals worldwide who experienced a recent cybersecurity incident due to an insider threat. Of those surveyed, 63% said they are worried about unmanaged IoT devices resulting in the loss of sensitive data, by the cloud (52% of respondents) and the network (51%). The findings show threats rose 44% over the past two years, with costs per incident up more than a third to $15.38 million.”
-
Data Breaches:
IoT applications, sensors, and devices gather various user data that are sensitive in nature. Moreover, it requires robust encryption to secure sensitive information to operate and process the data.
-
Data Authentication:
Although devices have encryption to protect the data, they may still be susceptible to hackers and illegal activities. As a result, it is pivotal to have a robust, authentic, and verifying process in place during communication or transference of data.
-
Side-Channel Threats:
Further, specific data and information are prone to attacks depending on the system operations.
-
Irregular Updates:
It is absolutely pivotal for IoT devices to be regularly updated to maintain a secure and advanced function. For instance, “The famous SolarWinds’s Supply Chain attack of 2020 which infected over 18,000 companies and government agencies using updates of office applications, and network monitoring tools.”
-
Malware and Ransomware:
Malware is malicious software that attacks a device and impacts its functions. On the other hand, ransomware seizes the user out of their device and requests a “ransom” to release it. In other words, one infects a device to affect function, and the other hijacks the system for an unfair monetary exchange.
Combining IoT with Quantum Computing
According to Gartner, “The use of atomic quantum states to effect computation. Data is held in qubits (quantum bits), which have the ability to hold all possible states simultaneously. Data held in qubits is affected by data held in other qubits, even when physically separated. This effect is known as entanglement.”
Moreover, SonicWall the American Cybersecurity company reports, “IoT malware volume rose 6% in 2021, totaling 60.1 million hits by year’s end. While this isn’t good news, it’s at least better than it has been: In 2019 and 2020, IoT malware volume rose 218% and 66%, respectively.” It also reports 24-hour statistics of World wide attacks that update each minute in the SonicWall Security Center.
Further, the challenge now is to identify, monitor, and ensure quality in IoT security. Moreover, there is a significant rise in data and information transfer due to a rise in the number of devices. Hence, there is a requirement for responsive, scalable, analytical, and efficient solutions.
As a result, Quantum Computing can make a pivotal change in the security and protection of data within IoT systems. It can also create a new infrastructure built with IoT and Quantum Computing networks. Therefore, this network includes four layers and they are:
-
Application Layer:
Firstly, the layer includes the application, its monitoring system, and a user’s system. It also creates the layer to transfer and easily enable the flow of data and information. Moreover, it sends and receives commands from the user via qubits.
-
Quantum Teleportation Layer:
Moreover, the quantum teleportation layer only incorporates quantum repeaters. That is to say, it manages the integrity of the qubits to process and transfers the data. Although, qubits may lose their entanglement during transfers. As a result, quantum repeaters play a pivotal role.
-
Quantum Network Layer:
The quantum network layer is responsible to monitor data transfers through quantum and classical systems. It also includes monitoring data within local networks and the internet. Moreover, it includes two components:
-
-
- Quantum Server: It incorporates quantum devices that analyze and manage quantum data. It also supports functions to operate and convert bits into qubits and vice versa.
- Gateway: It includes existing devices within a layer that function as gateways. For example, routers help transfer data from bits using physical layers to qubits that use quantum servers within the network layer.
-
-
Physical Layer:
Physical layers include any device, sensor, or component within the IoT system. Moreover, it maintains its state within the IoT network and helps transfer data throughout the layers.
IoT and Quantum Computing Solutions
Further, Quantum Computing can use its potential to address the challenges and bottlenecks affecting IoT. Hence, here are a few solutions:
-
Optimum Complex Computation Capabilities:
Quantum Computing enables the increase in the speed of processing data. Moreover, IoT systems highly appreciate and require rapid results as they generate heavy volumes of data. Therefore, Quantum Computing plays a pivotal role in processing simple and complex data faster within the IoT system.
-
Rapid authentication and Verification Procedure:
Quantum computing also acknowledges the requirement of speed in the IoT process. Therefore, quick authentication and verification ensure constant data security and process optimization. It also maintains security and protection throughout the system.
-
Protecting Confidential Communications:
The more secure the communication the more it enables the use of quantum cryptography. Hence, the complex nature of the system defends it from attacks and malpractices.
Conclusion:
In conclusion, IoT and Quantum Computing combine their functions to protect and secure IoT systems. Although still under development, the increase in the demand and usage of technology guarantees a better future for businesses and industries.
You May Also Like To Read:
Quantum Computing and Healthcare: Learn more about these Applications
Myths vs. Reality of Quantum Computing