MADRID, Spain, April 17, 2024 — HashiCorp, Inc. (NASDAQ: HCP), a leading provider of multi-cloud infrastructure automation software, announced today the...
Tag - technology
Somerset, UK, April 15, 2024 — In the fast-paced world of trading, staying ahead of the curve often hinges on accessing timely and accurate signals...
SINGAPORE, April 12, 2024 — Mobile-health Network Solutions (“MNDR” or “the Company”), a leading telehealth solutions provider in Singapore, today...
Dubai, UAE, April 12, 2024 — In the realm of cryptocurrency and digital asset trading, legitimacy and trustworthiness are paramount considerations for...
SINGAPORE, April 12, 2024 — Genius Group Limited (NYSE American: GNS) (“Genius Group” or the “Company”), a leading AI-powered education group, today...
With the integration of Mastercard Move, commercial banks and payers can leverage faster and more secure payouts via Verituity’s white label payments platform...
StakingFarm is set to revolutionize the crypto market by launching Staking-as-a-Business, designed to cater to both institutions and individual investors. CEO...
Cloud, also known as ‘The Cloud,’ is a revolutionary platform that countless businesses utilize. It’s a frontrunner in developing, managing...
Alliance formed to accelerate development of augmented reality eyewear applications PISCATAWAY, N.J., April 11, 2024 — The AR Alliance announces that...
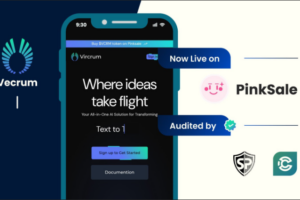
Dubai, UAE, Vircrum revolutionizes content creation, translation, and summarization, empowers visual storytelling and data visualization, enhances...